Guide to Using S/MIME
Newsgroup: mozilla.dev.tech.cryptoTechnical contacts: Javier Delgadillo and Terry Hayes
Manager: Stephane Saux
Contents
Introduction
Getting Started
Signing and Encrypting Email Messages
Obtaining Encryption Certificates for Email Recipients
What To Test
Appendix A: Viewing Certificates
Appendix B: Troubleshooting
Introduction
Nightly Mozilla builds now include basic S/MIME functionality. See Encryption and Signing UI Specifications for information on our UI plans. This document describes how to use and test S/MIME in the current Mozilla builds.
Netscape has set up a public Test Certificate Authority (CA) specifically for the purpose of testing S/MIME in Mozilla nightly builds. This CA issues test certificates that expire after ten days. This section describes how to obtain dual-key test certificates from the CA and configure Mail & Newsgroups so you can send signed and encrypted email messages.
To set up the browser for testing S/MIME and obtain the appropriate certificates from Netscape's test CA, follow these steps:
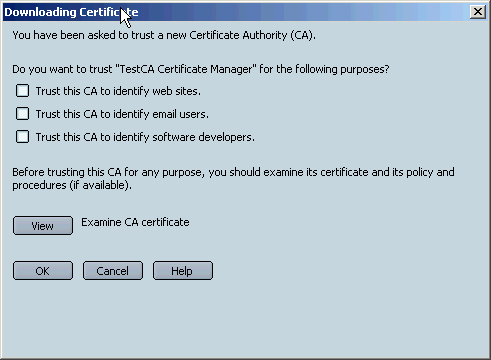
Select the first two checkboxes, at a minimum. Doing so indicates that you trust this CA certificate to
identify web sites and email users. You can then can visit the SSL server for the
Netscape Test CA without triggering a warning. More importantly, selecting these trust settings also
ensures that you can vaildate signed emails from other people whose certificates were issued by the
Netscape Test CA. The Netscape Test Certificate Authority will issue you dual-key certificates.
This means that you get two certificates: one used by other people to encrypt emails they send to you, and the other used by you to sign emails and to identify yourself to servers that require client authentication.
Note that it's possible to obtain a single certificate that supports signing and encryption. For example, free trial email certificates from Verisign support both signing and encryption. However, thorough testing of S/MIME requires testing dual-key certificates.
If you have problems obtaining a certificate from the Netscape Test Certificate
Authority, send an email to testca-admin@netscape.com
Back up your certificates. You should also back up your test certificates. To do so, open the Certifiate Manager, select both your new certificates, and click Backup. This is very important. If something happens to your certificate database or you have any other problems, you will lose access to encrypted emails unless you can restore the backup copy of your certificates.
Once you've obtained your test certificates, you should take a look at them using the Certificate Manager. Follow these steps:
For more information on many aspects of using certificates, open the Help menu, choose Help and Support Center, and double-click Using Certificates in the left frame. Current builds do not yet include S/MIME help, but you can find information on general certificate management.
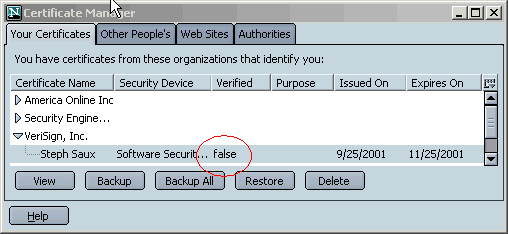
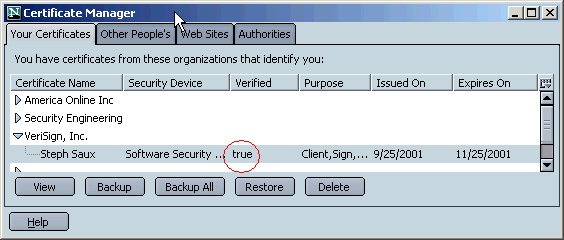
Under the Your Certificates tab in the Certificate Manager, the 'Verified' column for your certificate must have the value "true" or you won't be able to use it. If the value for either of your dual-key certificates is not "true," see the
Troubleshooting section of this document.
To test your signing certificate for client authentication, click this link and log into the test server:
client authentication test server.
Normally the process of client authentication is transparent to the user. To see certificate request dialog, you must follow these steps before authenticating:
If you have previously authenticated to the test server during the same session, you will need to exit the browser, relaunch it, and visit the page (linked above) again.
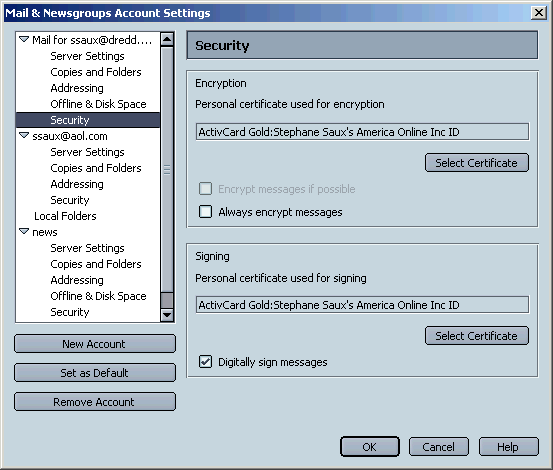
To send signed or encrypted emails, you must first configuring your one of your mail accounts for S/MIME. Follow these steps:
The Security panel contains two sections: Digital Signing and Encryption:
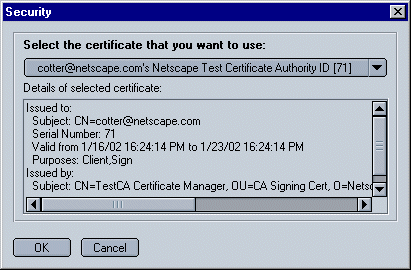
This dialog box appears:
You must select both a signing certificate and an encryption certificate before you can start sending signed messages. When you sign a message, both your encryption and signing certificates are attached to theit, so that recipients can can both verify your digital signature and, if they wish, send you encrypted email.
You are now ready to send signed and encrypted messages. A new Compose window opens. If you followed the directions in this document exactly, you'll notice that Digitally Sign is already checked, because of the Mail & Newsgroup Account option you selected earlier.
If you want to digitally sign the message only, without encrypting it, you don't need to do anything with this menu (assuming that the Digitally Sign item is already selected). If you want to encrypt the message as well as signing it, select Always Encrypt. (In current builds, Always Encrypt applies to this Compose window only.) When you receive a message, the right side of the heading area (in current builds) indicates whether the message is signed or signed and encrypted. (Encrypted messages are always signed.)
If you have configured S/MIME as described above, you can digitally sign any emailmessage. To encrypt a message, however, you must already have an encryption certificate for each of the recipients. The next section describes how to obtain recipients' certificates.
The current S/MIME implementation provides two ways to obtain the encryption certificate that you need before you can send encrypted email to a given recipient. Some suggestions for testing:
For each reading/sending test you run, please consider the following
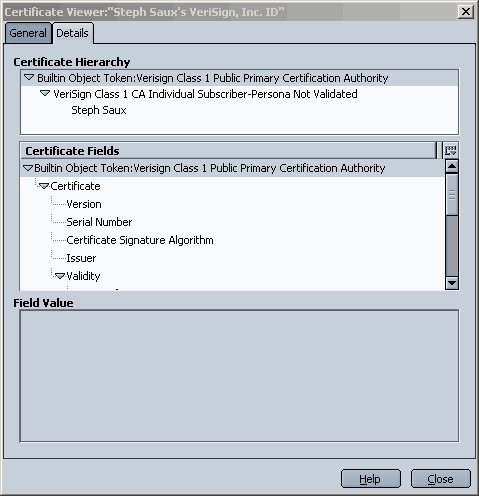
cases: To open the Certificate Manager and perform basic management tasks, follow these steps: The Details tab of the Certificate Viewer
shows the certificate hierarchy for the certificate chain. This is
useful when you're attempting to locate a root CA certificate so you can edit
its trust attributes.
For more information on many aspects of using certificates, click Help in any dialog box or open the Help menu, choose Help and Support Center, and double-click Using Certificates in the left frame. Current builds do not yet include S/MIME help, but you can find information on general certificate management.
If you have problems reading or sending signed/encrypted messages, it's probably because the certficates used for the S/MIME operation that is failing are not "Verified,", which means that they do not chain to a trusted root. Due to some PSM bugs, importing a certificate may cause the root CA certificate to loose its trust settings (101616, 100386) These are not S/MIME bugs, and they're being worked on, but you'll need
to work around them until they are fixed.
If your Free trial Verisign Cert does not verify, the Certificate ManagerWindow may look like this:
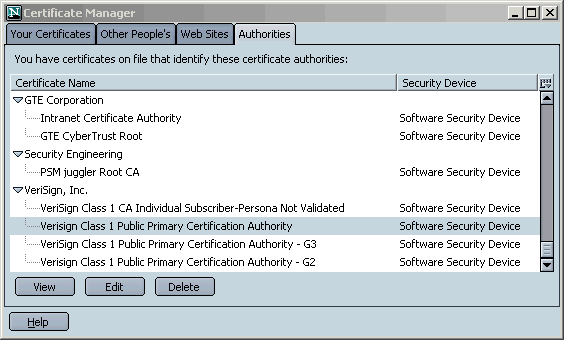
If this is the case, click the Authorities Tab and locate the root CA cert for Verisign personal email certificates:
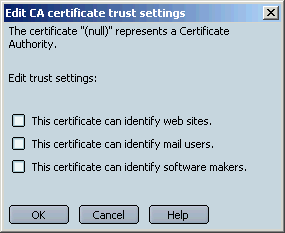
When you select the root certificate and click Edit, you will see something like this:
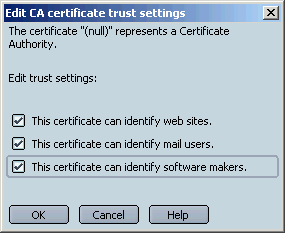
Since none of the trust options are selected, your browser doesn't trust this certificate. This is due to a PSM bug. This CA certificate is normally built-in and trusted by the browser. To fix the problerm, select all three checkboxes, like this, then click OK:
If you go back to the Your Certificates tab, youll now see something like this: Once you have done this, your certificate is trusted, and you can sign your emails. Other people's Verisign certificates will also be trusted, and you'll be able to encrypt mail to them.
As we start implementing the full S/MIME UI, we would like to solicit help from the MOzilla community in ongoing testing of S/MIME features. The rest of this document describes how to
Getting StartedDownload the CA Certificate and Configure S/MIME
Examine Your Certificates and Test Client Authentication
Configure a Mail Account for S/MIME
To digitally sign an email message, follow these steps:
Signing and Encrypting Email Messages
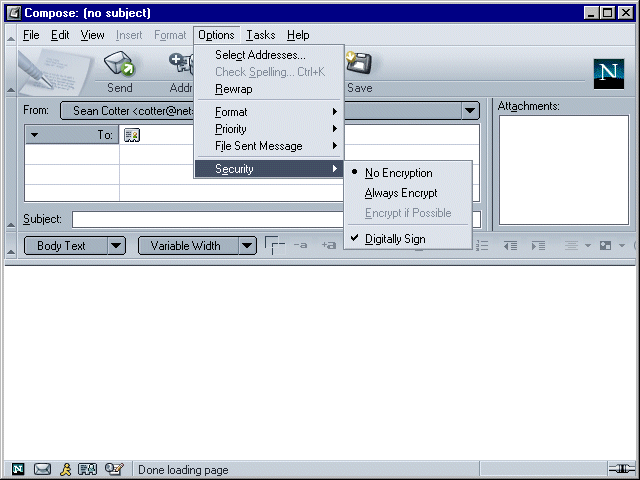
Obtaining Encryption Certificates for Email Recipients
To determine whether you have someone's certificate, open the Certificate Manager as described above and click the Other People's tab.
What To Test
Appendix A: Viewing Certificates.
Appendix B: Troubleshooting.